On Monday, Motorola announced its plans to form an information sharing and analysis organization (ISAO) to help fight cyber crime in the public sector.
About the organization
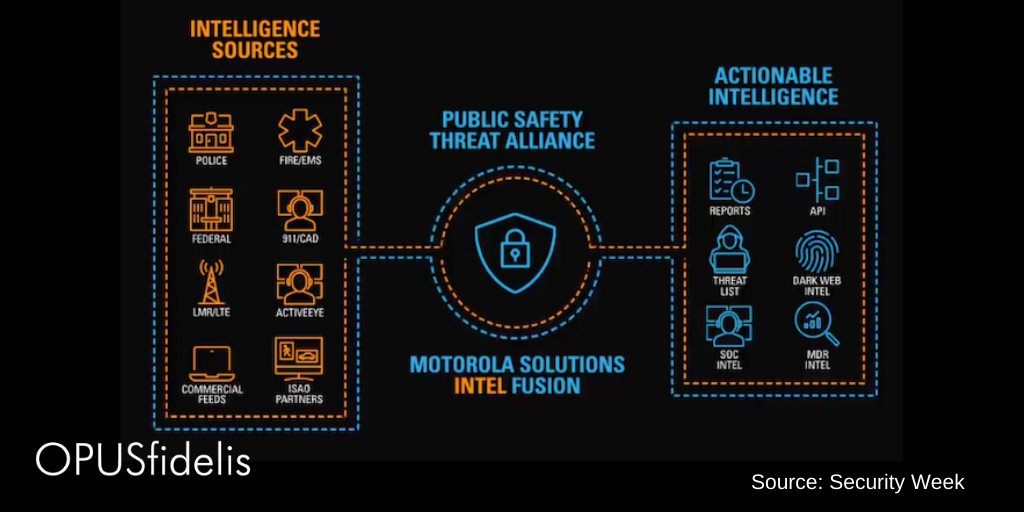
Dubbed the Public Safety Threat Alliance (PSTA), the organization seeks to strengthen public safety organizations’ cybersecurity plans and responses through the sharing and analyzing of collective data. As Security Week reported:
“Information is collected from various sources, including law enforcement, EMS, mobile communications systems, commercial security products, and ISAO partners. The information is used to create actionable intelligence, including reports, APIs, threat lists, dark web intel, SOC intel, and MDR data.”
After last year’s drastic increase in cyber threats to government agencies, Motorola decided to form the PSTA so that public agencies could better fortify their defenses by sharing information about their cyber security experiences. Scott Kaine, corporate vice president of Cybersecurity at Motorola Solutions stated:
“[I]t’s been reported that there was a 1,885 percent increase in ransomware attacks against governments worldwide in 2021… With cyber threats increasing in scope, scale and complexity, the Public Safety Threat Alliance can help to dramatically increase the efficacy with which intelligence is used to monitor, detect and respond to potential threats before they result in downtime of public safety services.”
Any public safety agency can become a member of the alliance, which has been recognized by the U.S. government’s Cybersecurity and Infrastructure Agency (CISA). As Billy Bob Brown, Jr., executive assistant director for Emergency Communications at CISA recently shared:
“The establishment of the Public Safety Threat Alliance fills a critical void, creating a single entity entirely focused on the collection, analysis, production and sharing of actionable public safety-focused cyber threat information and intelligence… Now, the public safety community is better equipped to focus their cyber threat intelligence and defense efforts on specific adversaries and their malicious cyberattacks.”